5 Steps to a Secure Lifecycle Review
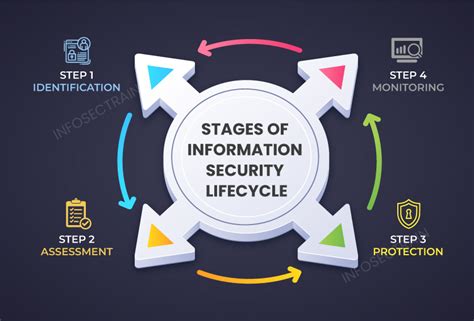
Understanding the Importance of a Secure Lifecycle Review

In today’s digital age, companies are collecting and processing vast amounts of sensitive data, making cybersecurity a top priority. A secure lifecycle review is a critical process that helps organizations identify and mitigate potential security risks throughout the entire lifecycle of their products or services. In this article, we will outline the 5 essential steps to conduct a comprehensive secure lifecycle review.
Step 1: Define the Scope and Goals of the Review
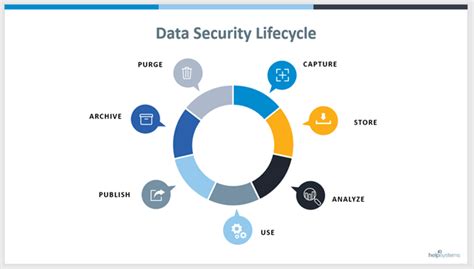
The first step in conducting a secure lifecycle review is to define the scope and goals of the review. This involves identifying the specific products or services to be reviewed, the stakeholders involved, and the desired outcomes. Clearly defining the scope and goals will help ensure that the review is focused and effective.
Some key considerations when defining the scope and goals include:
- Identifying the specific products or services to be reviewed
- Determining the stakeholders involved, including development teams, security teams, and external partners
- Establishing the desired outcomes, such as identifying security vulnerabilities or improving compliance
🔒 Note: It's essential to involve all relevant stakeholders in the review process to ensure that all perspectives are considered.
Step 2: Gather Information and Data

The next step is to gather information and data about the products or services being reviewed. This includes collecting documentation, conducting interviews with stakeholders, and analyzing relevant data.
Some key sources of information to gather include:
- Product or service documentation, such as design specifications and technical documentation
- Stakeholder interviews, including development teams, security teams, and external partners
- Relevant data, such as security logs and incident reports
📊 Note: It's essential to gather accurate and comprehensive information to ensure that the review is thorough and effective.
Step 3: Identify Security Risks and Vulnerabilities
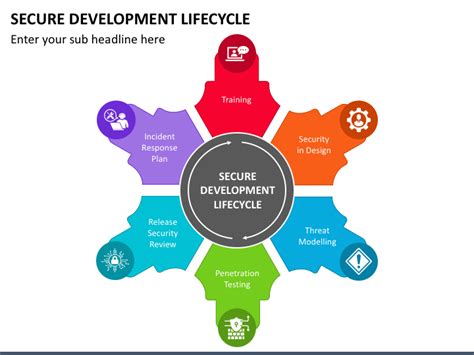
The third step is to identify security risks and vulnerabilities associated with the products or services being reviewed. This involves analyzing the gathered information and data to identify potential security threats.
Some common security risks and vulnerabilities to consider include:
- Data breaches and unauthorized access
- Malware and ransomware attacks
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks
- Insider threats and privilege abuse
| Security Risk | Description |
|---|---|
| Data Breaches | Unauthorized access to sensitive data |
| Malware and Ransomware Attacks | Malicious software designed to harm or extort organizations |
| Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks | Overwhelming a system with traffic to make it unavailable |
| Insider Threats and Privilege Abuse | Authorized individuals intentionally or unintentionally compromising security |
Step 4: Prioritize and Mitigate Security Risks
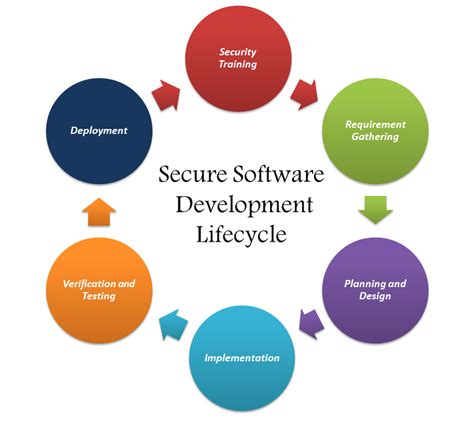
The fourth step is to prioritize and mitigate the identified security risks and vulnerabilities. This involves determining the likelihood and potential impact of each risk and implementing controls to mitigate or eliminate them.
Some key considerations when prioritizing and mitigating security risks include:
- Determining the likelihood and potential impact of each risk
- Implementing controls to mitigate or eliminate risks, such as security patches, firewalls, and access controls
- Monitoring and reviewing the effectiveness of implemented controls
🔒 Note: It's essential to prioritize and mitigate security risks in a timely and effective manner to prevent security incidents.
Step 5: Review and Refine the Secure Lifecycle Review Process
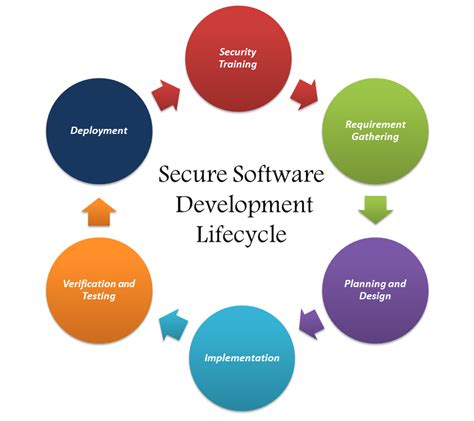
The final step is to review and refine the secure lifecycle review process. This involves evaluating the effectiveness of the review process and identifying areas for improvement.
Some key considerations when reviewing and refining the secure lifecycle review process include:
- Evaluating the effectiveness of the review process in identifying and mitigating security risks
- Identifying areas for improvement, such as incorporating new security controls or improving stakeholder engagement
- Refining the review process to ensure it remains effective and efficient
A secure lifecycle review is an essential process that helps organizations identify and mitigate potential security risks throughout the entire lifecycle of their products or services. By following these 5 steps, organizations can ensure that their secure lifecycle review process is comprehensive and effective.
As we summarize the key points, it’s clear that a secure lifecycle review is a critical process that requires careful planning, execution, and review. By following these steps, organizations can ensure that their products or services are secure and resilient, protecting their customers, employees, and reputation.
What is a secure lifecycle review?
+
A secure lifecycle review is a comprehensive review process that helps organizations identify and mitigate potential security risks throughout the entire lifecycle of their products or services.
Why is a secure lifecycle review important?

+
A secure lifecycle review is essential to identify and mitigate potential security risks, protecting an organization’s customers, employees, and reputation.
How often should a secure lifecycle review be conducted?
+
A secure lifecycle review should be conducted regularly, ideally annually or bi-annually, to ensure that security risks are identified and mitigated in a timely manner.