The Jester Hacker: Exposing Online Vulnerabilities

The Rise of the Jester Hacker
In the vast expanse of the internet, a new breed of hacker has emerged, shattering the traditional notion of malicious cyberattacks. Meet the Jester hacker, a unique entity that has been making waves in the online community with their unconventional approach to hacking. Unlike their counterparts, Jester hackers don’t seek financial gain or notoriety; instead, they focus on exposing online vulnerabilities to force change and promote digital security.
Who is the Jester Hacker?

The Jester hacker, also known as “th3j35t3r,” is a self-proclaimed “hacktivist” who has been active since 2010. This enigmatic figure has gained significant attention for their high-profile hacks on various websites, including those of extremist groups, corrupt governments, and compromised networks. The Jester’s true identity remains unknown, but their motivations and methods have sparked intense debate among cybersecurity experts and enthusiasts.
Methods and Motivations

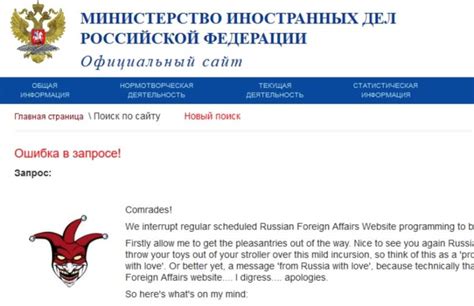
The Jester hacker’s approach is characterized by their use of SQL injection attacks, DNS hijacking, and other sophisticated techniques to infiltrate vulnerable systems. Once inside, they often leave behind a signature taunting message, emphasizing the need for improved security measures. Unlike malicious hackers, the Jester does not exploit vulnerabilities for personal gain or to cause harm; instead, they aim to expose weaknesses and encourage organizations to fortify their defenses.
Key characteristics of the Jester hacker’s methods:
- Targeting high-profile websites and networks to maximize impact
- Using advanced hacking techniques to demonstrate vulnerabilities
- Leaving behind signature messages to raise awareness and promote change
- Avoiding financial gain or personal notoriety
High-Profile Hacks and Controversies

The Jester hacker has been involved in several high-profile hacks, including:
- Anonymous and LulzSec: The Jester has been a vocal critic of these groups, claiming that their actions are more focused on causing chaos than promoting positive change.
- WikiLeaks: The Jester has hacked into WikiLeaks’ website, criticizing the organization’s handling of sensitive information and lack of security measures.
- Extremist groups: The Jester has targeted various extremist groups, including the Taliban and al-Qaeda, to disrupt their online presence and expose their vulnerabilities.
Criticism and Controversy

While some view the Jester hacker as a heroic figure, others criticize their methods as reckless and irresponsible. Some argue that the Jester’s actions can lead to unintended consequences, such as:
- Unintended harm: The Jester’s hacks can inadvertently cause harm to innocent parties or disrupt critical infrastructure.
- Lack of accountability: The Jester’s anonymous nature and unorthodox methods make it difficult to hold them accountable for their actions.
🤔 Note: The Jester hacker's actions have sparked intense debate, with some viewing them as a force for good and others seeing them as a menace. As with any complex issue, it's essential to consider multiple perspectives before forming an opinion.
The Impact of the Jester Hacker

Despite the controversy surrounding the Jester hacker, their actions have undoubtedly raised awareness about the importance of online security. By exposing vulnerabilities and pushing organizations to improve their defenses, the Jester has contributed to a more secure digital landscape.
Key takeaways from the Jester hacker’s impact:
- Increased awareness: The Jester’s hacks have brought attention to the need for robust security measures and the consequences of neglecting them.
- Improved security: Organizations have been forced to reevaluate and strengthen their defenses in response to the Jester’s exploits.
- A new approach to hacktivism: The Jester’s methods have inspired a new wave of hacktivists who focus on promoting positive change rather than causing chaos.
Conclusion
The Jester hacker’s unconventional approach to hacking has sparked intense debate and raised important questions about the role of hacktivism in promoting digital security. As the online landscape continues to evolve, it’s essential to consider the Jester’s methods and motivations, as well as the potential consequences of their actions. Ultimately, the Jester hacker’s impact serves as a reminder of the need for robust security measures and the importance of responsible hacking practices.
What is the Jester hacker’s true identity?

+
The Jester hacker’s true identity remains unknown. Despite numerous attempts to uncover their identity, the Jester has managed to maintain their anonymity.
What is the Jester hacker’s motivation?
+
The Jester hacker’s primary motivation is to expose online vulnerabilities and promote digital security. They aim to force organizations to improve their defenses and raise awareness about the importance of robust security measures.
Is the Jester hacker a malicious actor?
+
No, the Jester hacker is not considered a malicious actor. While their methods may be unorthodox, their primary goal is to promote positive change and improve digital security, rather than causing harm or exploiting vulnerabilities for personal gain.



